In today's world, the highly digital and dynamic business environment has increased the demand for enterprise identity management and system integration than ever. Many organizations are using their systems in a remote-work ecosystem for the first time. Social distancing efforts to contain the COVID-19 pandemic have driven shoppers online in record-breaking numbers, accelerating the business's digitalization. The customer self-service portal becomes the key to lower operating costs, improve effectiveness, and reduce contact volume and expenses. To solve these challenges, you will need:
- A robust identity management solution to keep your data safe
- Centralized identity management to store and manage the users
- Single Sign-On (SSO) across multiple systems
- Single point of entry for users to bring all the systems together to serve your users
The Role of Liferay in Enterprise Identity Management and System Integration
Together with an enterprise identity management system, Liferay can be used as a solid foundation to solve those challenges. With its strong integration capabilities, Liferay can bring all the different systems together to provide a single point of entry and unified user experience. The enterprise identity management solution can give strong cybersecurity, centralized user identity management, and SSO across multiple systems. You can quickly integrate all the different systems together and create an enterprise business solution including but not limited to:
- Self Service Customer Portal
- Employee Portal/Intranet Portal
- B2B Portal/Vendor Portal
- E-Commerce Portal
- Etc.
Today we will talk about how Liferay works with the identity management system in the enterprise environment.
Liferay Enterprise Identity Management Architecture
Liferay can be used as either the Identity Provider (IdP) or as the Service Provider (SP).
Identity Provider (IdP) – The Identity Provider is a system that provides authentication services. It authenticates the user and provides an authentication token (that is, information that verifies the authenticity of the user) to the service provider.
Service Provider (SP) – A Service Provider is the business application. The SP requests the authentication from the identity provider.
If you don't have an existing IdP yet, you can consider using Liferay as the IdP to save some cost. Liferay can work as an IdP with the SAML 2.0 protocol. The architecture looks like below:
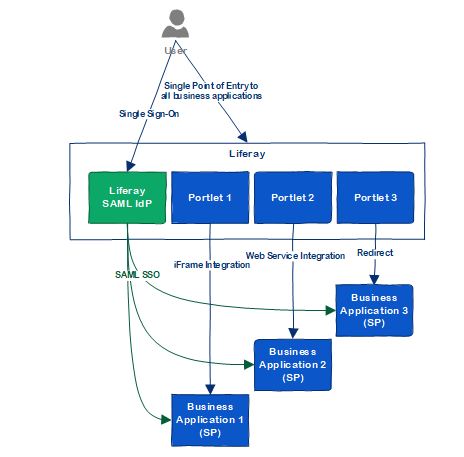
But if you already have an IdP, or plan to use a 3rd party IdP, Liferay can be a service provider and integrate with the 3rd Party IdP easily:
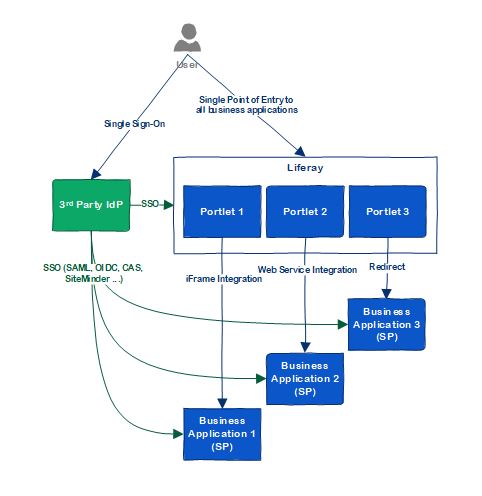
Single Sign-On
One of the crucial parts of this solution is Single Sign-On. It gives the users a seamless experience when navigating between different systems without typing their password again and again.
Which Single Sign On (SSO) protocols do Liferay support?
Liferay supports a variety of SSO protocols, including:
SAML 2.0
Security Assertion Markup Language (SAML) is an XML-based open-standard that provides authentication between an IdP and a service provider. It is one of the major authentication protocols used today.
Note: To use SAML 2.0, you need to install the Liferay Connector to SAML 2.0 from Liferay Marketplace. Liferay Enterprise Edition Subscription is required.
OpenID Connect
OpenID Connect is a lightweight authentication layer built on top of the OAuth 2.0 authorization protocol. It compliments having local accounts by enabling users to authenticate using accounts they have on other systems. Users who avoid signing up for new accounts can then use an account they already have to sign into your website. By using OpenID Connect, you delegate user authentication to other providers, making it easy for users with existing accounts to authenticate to your system.
CAS
CAS is an authentication system originally created at Yale University. It is a widely used open source single sign-on solution and was the first SSO product to be supported by Liferay DXP. Liferay DXP’s CAS module includes the CAS client, so there’s no need to install it separately.
OpenAM
OpenAM is an open source single sign-on solution that comes from the code base of Sun’s System Access Manager product (Now ForgeRock Access Management). Liferay DXP integrates with OpenAM, allowing you to use OpenAM to integrate Liferay DXP into an infrastructure that contains a multitude of different authentication schemes against different repositories of identities.
Token-Based SSO (e.g. SiteMinder)
Token-based SSO authentication was introduced in Liferay DXP 7.0 to standardize support for Shibboleth, SiteMinder, Oracle OAM, or any other SSO product that works by propagating a token via one of the following mechanisms:
- HTTP request parameter
- HTTP request header
- HTTP cookie
- Session attribute
NTLM
NTLM (NT LAN Manager) is a suite of Microsoft protocols that provide authentication, integrity, and confidentiality for users. Though Microsoft has adopted Kerberos in modern versions of Windows server, NTLM is still used when authenticating to a workgroup. Liferay DXP now supports NTLM v2 authentication. NTLM v2 is more secure and has a stronger authentication process than NTLMv1.
Note: NTLM authentication was deprecated in Liferay DXP 7.2 and was removed. You can still install it from Marketplace here.
Comparing the different Single Sign-On protocols
Just-in-Time Provisioning
Just-In-Time (JIT) provisioning enables automatic user account creation in Liferay the first time a user logs in with SSO. With JIT provisioning, IT admins no longer need to create accounts manually for each user in each application they use. JIT provisioning can play a key role in automating IT workflows and saving time.
With Liferay, the JIT provisioning is implemented with LDAP integration for most of the SSO protocols. It requires:
- All users must be stored in a LDAP server
- Both Liferay and the IdP must be connected to the LDAP server
Some of our clients do not use LDAP or do not want Liferay to talk to their enterprise LDAP directly. Dunn Solutions has implemented a JIT provisioning plugin, which helped the client to solve the problem. The plugin reads the user profiles information from the SAML attributes or OIDC attributes during the login and automatically creates the Liferay user.
Single Log Out (SLO)
Single Log Out is an important part of the SAML standard. Organizations rely on SLO to ensure that distributed user login sessions are properly terminated when users log out from either the Identity Provider or a specific application in the SSO ecosystem.
OOTB Liferay supports SLO with SAML 2.0 and CAS protocols.
For Token-Based SSO like SiteMinder or F5, SLO is implemented by nature. The web proxy in front of Liferay will automatically stop the user from accessing any applications once log out.
For OIDC, Liferay's current OIDC integration does not support SLO because the SLO-related specifications in OIDC are currently in draft, different providers may have varying methods of supporting this functionality, or some may not support it at all. Dunn Solutions has implemented custom plugins for our clients against various IdPs, such as Okta, NetIQ and others.
Support Multiple IdPs
It is often the case that, when running as a Service Provider, your Liferay portal is required to connect with multiple Identity Providers. OOTB Liferay, only OIDC protocol supports multiple IdPs. Some of our clients who use CAS and SAML protocols found the limitation and asked Dunn Solutions for help. Dunn helped the clients to implement custom plugins to support multiple IdPs with SAML/CAS protocols and provided guidance to configure the connections between Liferay and multiple IdPs.
Below is the comparison of the Single Sign-On protocols that supported by OOTB Liferay:
|
|
Just-in-Time Provisioning
|
Support Single Log Out
|
Support Multiple IdPs
|
Other limitations
|
|
SAML 2.0
|
Supported via LDAP
|
Yes
|
No
|
|
|
OpenID Connect
|
No
|
No
|
Yes
|
|
|
CAS
|
Supported via LDAP
|
Yes
|
No
|
|
|
OpenAM
|
Yes
|
No
|
No
|
|
|
Token-Based SSO (e.g. SiteMinder)
|
Supported via LDAP
|
Yes
|
No
|
|
|
NTLM
|
No
|
No
|
No
|
Windows only
|
3rd party IdPs that works with Liferay
Liferay is IdP agnostic. As long as the IdP supports one of the SSO protocols above, Liferay can work with it. Below are some of the 3rd Party IdPs that we worked with:
|
Product
|
Supported SSO protocols
|
|
Microsoft ADFS
|
SAML, OIDC
|
|
OKTA
|
SAML, OIDC
|
|
CAS
|
SAML, OIDC, CAS
|
|
ForgeRock Access Management
|
SAML, OIDC, OpenSSO
|
|
NetIQ
|
SAML, OIDC
|
|
Keycloak
|
SAML, OIDC
|
|
OneLogin
|
SAML, OIDC
|
|
Oracle Identity Management
|
SAML, OIDC
|
|
SAP Customer Data Cloud
|
SAML, OIDC
|
|
Auth0
|
SAML, OIDC
|
|
F5
|
Token-Based
|
|
SiteMinder
|
Token-Based (SiteMinder)
|
|
|
|
Contact Dunn Solutions today to learn more about the value Liferay brings!



